Now we can never be too careful, after spending all night downloading ten’s of gigabytes of random company databases the last thing anyone would want is to have their door kicked in by whatever gestapo resides in your home country, and have them cart away your beloved computer only to find all of your prized data intact along side whatever dodgy fetish porn you also have on their. But lets be honest, if you got caught that’s your own fault. But having your data no-so-easily recovered, well that’s a pretty easy feat to achieve.
All joking (heh) aside, you wouldn’t want everything on your laptop open to the world because some delinquent bell-end on a scooter decided to lift your bag as you left some trendy London coffee shop with your soy-boy latte. Full disk encryption is something that should be practised by all, privacy is your right, but it is also your responsibility.
There are many programs out there that can be employed to ensure that your hard drive is rendered completely secure to anyone that does not know the password.
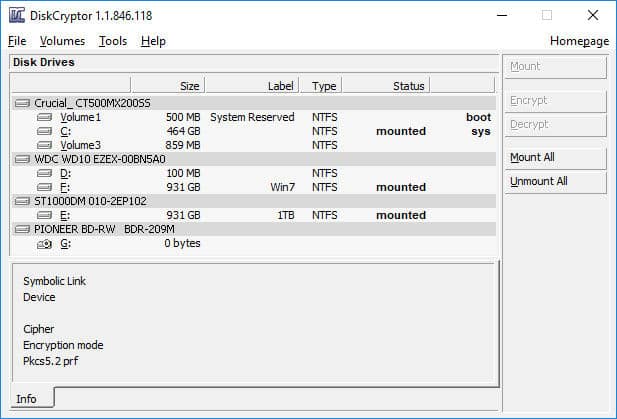
For this article we will focus on Diskcryptor (discontinued) – New URL of updated version here https://www.diskcryptor.org/ it’s a program that i’ve been using for the last few years, and despite its few flaws, this open source program does exactly what it says on the tin.
Flaws you say? what could they be? Well fortunately for me, my arcane motherboard does not use one of those security risk UEFI BIOS, something that Diskcryptor does not support – UPDATE V1.2b3 does along with a few other improvements, so if you wish to deploy it on your system you will no longer have to set your BIOS to Legacy and convert GPT to MBR
This overall isn’t a major issue, I’ve ran the program on both HDD and SSD set up’s, and thanks to it utilizing hardware accelerated AES from the CPU, I’ve noticed no degradation in machine speed, of course we can deploy a multiple of algorithms, including my old favourite Serpent (as well as Twofish), you also have the option of mixing and matching several ciphers to suite your needs. Something i might consider when i finally pull my finger out and get a thread ripper along with a couple of new SSD’s, but i digress.
Now what algorithm, or algorithms you choose will depend on your level of need, machine speed, and general paranoia, i mean a cascade of all three would be wonderful and ensure that if any weakness is found in one it will not effect the others, however if you are running it on a shitty processor and with a 5400 rpm HDD that is about to die on you, then maybe that’s not the best option, but you get my drift.
If you opt for only AES, and your processor supports hardware acceleration, then you could easily be pulling several GB/s, this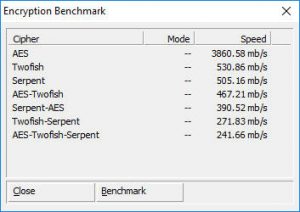 benchmark for example is using my much mocked AMD FX-4100 CPU. Using only AES allows you the option of installing a highly optimized bootloader coded in nothing more than assembly. If you use any other algorithm of combo of such, then it will use its standard bootloader, this said any modern system that is capable of running even windows XP shouldn’t see this as an issue. As you can see, even using an AES-Twofish combo would still run pretty smoothly.
benchmark for example is using my much mocked AMD FX-4100 CPU. Using only AES allows you the option of installing a highly optimized bootloader coded in nothing more than assembly. If you use any other algorithm of combo of such, then it will use its standard bootloader, this said any modern system that is capable of running even windows XP shouldn’t see this as an issue. As you can see, even using an AES-Twofish combo would still run pretty smoothly.
You have other options for installing it, you can stick if on a USB stick and use that to boot your encrypted machine which would allow you an extra layer of security if you wanted to go down that route.
Once installed you have the fun task of then encrypting your hard drive with your chosen password, if you are going to all this effort, please don’t do something shitty like use password or 123456, if you can aim for something a little more hard core, i mean if you can’t break it within a reasonable time using a 32 GFX card number cruncher then you should be good, aim for something 30 characters plus, i dare you.
Once you start the encryption process – which will take several hours depending on hard drive size, you can keep using your machine as normal, you won’t really notice any difference. You can pause the process if you wish, even reboot or shutdown the machine (assuming you have paused the process first) and pick up where you left off. If you do this and reopen the program it will point out that you are in the middle of an encrypt and ask to continue.
While you are at it, encrypt any other hard drives you have in the machine, if you use the same password they will be automatically mounted when you boot up. One nifty feature, you can encrypt ISO images and burn them to disk, handy if you want to dump all your porn selfies off your phone onto an uber-secret DVD image but don’t want some random scrote finding it at a party and uploading them all to your facebook wall.
Now a word of caution, while i don’t recommend any total noob tries to encrypt there drive, you might find with your set up its a little trial and error in regards to the boot loader etc, i mean the program is simple enough, it works fantastically, but there can always be… issues.
For this, you should always download and burn a copy of Hiren’s Boot CD while this disk itself could have an article on how useful it is, it has one handy feature, in that it has an earlier copy of Diskcryptor on it, this will allow you to decrypt your drive should something fuck up, if something does go wrong, if you decrypt the drive and use it to remove the boot loader you should be able to boot up normally again. If you want to grab a copy of Hiren’s Boot CD, i’ve lobbed it on our seedbox here since hiren’s site doesn’t seem to link too it, but if you’d rather pull a copy off mega.nz then grab it here.
Another thing worth noting, some of the windows updates, specifically the big important ones, do not like Diskcryptor being installed, it tends to get stuck in a kind of “choose your keyboard layout” loop each time you boot up, the only way around this sad endeavour is to decrypt the hard drive, reboot to finalize the install and then re-encrypt it. They fixed the update issue too! I cannot fault the program.
Remember however, should anyone get hold of your machine while you are logged in and the password entered, they will be able to dump them from memory, whether you lock down your machine to prevent installation or running of 3rd party programs is up to you, if you do then i guess i don’t have to tell you to superglue your ram in either. Oh and don’t forget to back up the headers onto a secure medium – just-in-case.
So there you have it, my recommendation for an FDE software package, its not cutting edge (2014 software) but its solid, its open source, it works. I’ve used it for years with out any real issue so hopefully it will do you too.